CraxsRat
Android Spyware
& RAT Detection Guide
Your device may be compromised. Learn to identify, detect, and perform Android RAT malware removal. Our guide helps you understand CraxsRat Android spyware and secure your data.
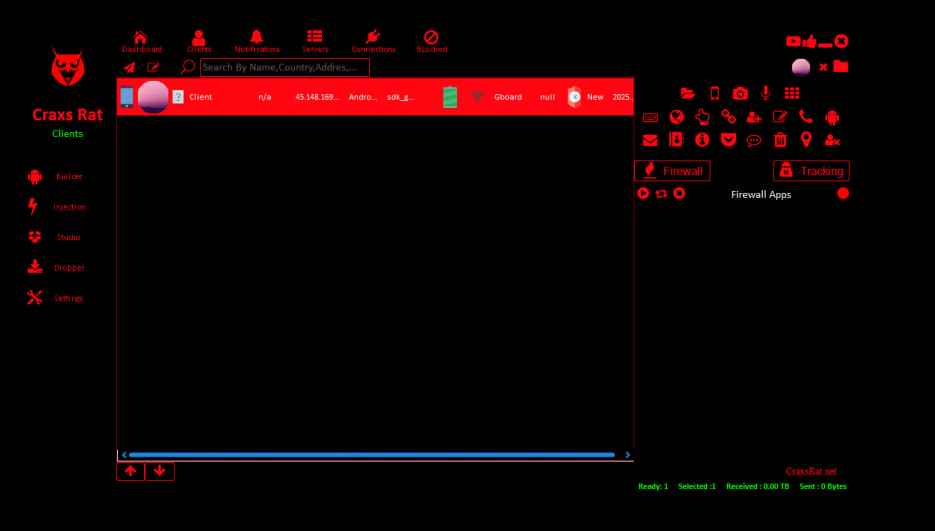
CraxsRat V7.4
Silent Spying In Progress...
Intelligence Analysis
Forensic evidence compiled from active malware samples
Remote Screen Control (VNC)
Attackers treat your device as their own. They can view your screen live, swipe, type, and open apps remotely even while the phone is locked.
Device Unlock & Screen Wake
Malware can forcibly wake your screen and unlock it using captured PINs or patterns to perform actions when you aren't looking.
Keylogging & Input Tracking
Logs every tap and keystroke. Attackers see everything you type: passwords, messages, search history, and 2FA codes.
Crypto & Banking Data Theft
Automatically detects and drains cryptocurrency wallets. It also intercepts SMS 2FA codes to bypass banking security.
File Exfiltration & Gallery Access
Silently uploads your photos, videos, and documents to a C2 server. Attackers can delete or encrypt your files for ransom.
Live Microphone & Camera Spying
Activates front/back cameras and microphone without indicators. Attackers can watch and listen to your surroundings in real-time.
3 Steps to Total Control
How a simple click turns into a total takeover.
Malicious Download / Sideloading
Users are tricked into downloading malicious APKs from fake websites, SMS phishing loops, or 'modded' app stores.
Dangerous Permissions
The malware requests 'Accessibility Service' privileges. Once granted, it can automate clicks, grant itself Admin rights, and prevent uninstallation.
Data Exfiltration & Control
The device connects to a Command & Control (C2) server. Attackers now have full remote access to steal files, credentials, and track location.
Complete Compromise in Under 60 Seconds
Once Accessibility is enabled, the automated infection script executes immediately. The device is fully compromised before the menu closes.
CraxsRat vs Others
See why CraxsRat is much more dangerous than other spyware apps.
| Capability | CraxsRat | Other RATs | Legit Apps |
|---|---|---|---|
| Remote Access Control (VNC) | |||
| Live Screen Mirroring | Sometimes | ||
| Keylogging & Passwords | |||
| SMS & 2FA Extraction | |||
| Overlay & Phishing Injection | Rarely | ||
| Stealth Mode & Persistence | Sometimes | ||
| Play Protect Bypass | Not well | ||
| Live Mic & Camera Feed | Only with Permit |
Remote Access Control (VNC)
Live Screen Mirroring
Keylogging & Passwords
SMS & 2FA Extraction
Overlay & Phishing Injection
Stealth Mode & Persistence
Play Protect Bypass
Live Mic & Camera Feed
Is My Phone Infected?
Answer these simple questions to see if spyware is hiding on your phone. It’s not a full scan, but it’s a great way to spot the warning signs.
⚠️ Disclaimer: This assessment is for educational guidance only and does not replace professional security software. If you suspect an infection, run a full scan with a reputable mobile antivirus immediately.
How to Keep Your Phone Safe
Stay one step ahead. Follow these simple tips to stop spy apps before they get inside.
Install Apps Only from Trusted Sources
Only download apps from the Google Play Store. Never install from suspicious links, Telegram channels, or 'cracked' APK sites.
Audit App Permissions
Immediately revoke permissions if a calculator or game asks for 'Accessibility' or 'Device Admin'. These are critical red flags.
Enable Google Play Protect
Ensure 'Google Play Protect' is active in your settings. It scans your device daily for known malware signatures.
Apply System Updates
Install Android security patches immediately. They fix critical vulnerabilities (CVEs) that spyware exploits to gain access.
Avoid Phishing & Smishing
Hackers use urgency. Verify the sender before clicking links in SMS or DMs. Never download files from unknown chats.
Use Reputable Mobile Security
Run periodic scans with established antivirus solutions (e.g., Avast, Bitdefender, Malwarebytes) to detect hidden threats.
Latest Articles
Read our newest articles and learn how to stay safe with our expert guides.
CraxsRat Architecture: Technical Analysis of Android Spyware
Hardening Android Devices Against RATs: A Comprehensive Defense Guide
Technical Analysis: How CraxsRat V7.4 Evades Google Play Protect
Daily Intelligence Feed
Get notified every time we drop a new malware analysis or security guide.